🔎 What Exactly Is HijackThis!?
HijackThis! (HJT) is a diagnostic tool used to scan your computer for specific areas commonly targeted by malware and browser hijackers. It identifies:
- ✅ Programs that automatically start with Windows
- ✅ Items that launch alongside your web browser
- ✅ Malicious entries in your Hosts file causing browser redirections
HijackThis! is powerful and should ideally be used by trained individuals. Logs generated by HijackThis! list both legitimate and potentially malicious entries, making correct interpretation critical. Mastering HijackThis! can significantly enhance your malware defense capabilities.
📋 Understanding a HijackThis! Log
HijackThis! logs divide into distinct categories, each indicated by a unique alphanumeric designation:
🌐 Internet Explorer & Browser Settings
- R0–R3: Internet Explorer Start/Search URLs and URL Search Hooks
- N1–N4: Netscape/Mozilla Start/Search URLs
- O1: Hosts file redirection
- O2: Browser Helper Objects (BHOs)
- O3: IE Toolbars
🚀 Startup Programs & Registry Entries
- F0–F3: Auto-loading programs via INI files and registry
- O4: Autostart entries from Registry
- O5: IE Options icon disabled in Control Panel
- O6: IE Options restricted by Administrator
- O7: Registry Editor access restricted
- O8: Extra IE context menu items
- O9: Extra buttons or menu items in IE
⚙️ Advanced System Modifications
- O10: Winsock Hijackers (LSP)
- O11: IE Advanced Options hijack
- O12: IE plugins
- O13: Default Prefix hijack
- O14: Reset Web Settings hijack
- O15: Trusted Zone hijacks
- O16: ActiveX Objects
- O17: DNS and Domain hijacks
- O18: Protocol hijacks
- O19: User stylesheet hijack
- O20: AppInit_DLLs, Winlogon Notify
- O21: ShellServiceObjectDelayLoad
- O22: SharedTaskScheduler
- O23: Malware installed as a Windows service
- O24: Windows Active Desktop components
📜 Example of a HijackThis! Log
Here is an example HijackThis! log:
https://pastebin.com/TP8kZUh9Code language: JavaScript (javascript)Here is an example infected HijackThis! log:
https://pastebin.com/S81FPxbwCode language: JavaScript (javascript)- ✅ Legitimate Entries: Trusted software and well-known services.
- ❌ Suspicious Entries: Unknown software, missing files, suspicious URLs.
🕵️♂️ How to Analyze a HijackThis! Log
Step 1: Identify Suspicious Entries
- ⚠️ O4 & O23: Check for unknown or suspicious startup programs and services.
- ⚠️ R0 & R1: Look for hijacked start/search pages.
- ⚠️ O1: Review for unwanted Hosts file modifications.
Step 2: Research Unknown Entries
- Search CLSIDs (found in O2/O3) online.
- Verify unknown services (O23) against known good services.
Step 3: Remove Entries with HijackThis!
- Select suspicious entries using checkboxes.
- Click Fix Checked to remove registry entries.
⚠️ Warning:
- HijackThis! removes only registry entries and startup references—not actual files.
- Always back up data or consult experts if unsure.
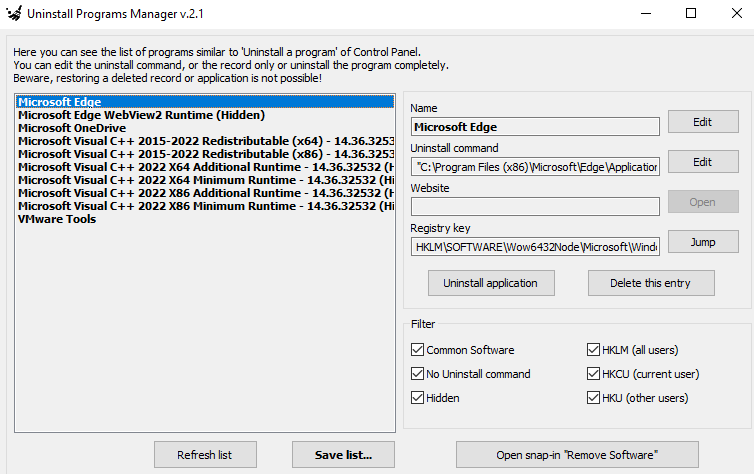
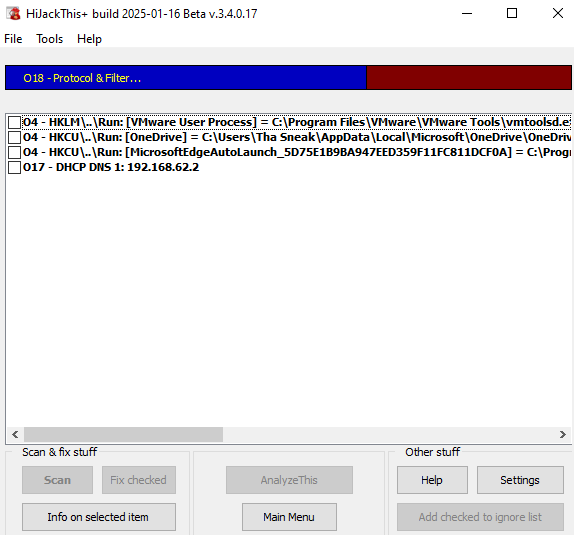
🖼️ Step-by-Step Image UI Guide
🛠️ Recommended Tools for Post-Log Malware Identification and Removal
Once a HijackThis! log is analyzed, these additional tools assist in further identifying and removing detected malware:
- 🔧 StartupList v2.13: Provides detailed startup diagnostics.
- 🔍 Process Explorer: Helps identify suspicious processes in real-time.
- 🚦 Autoruns: Thoroughly analyzes all programs and services set to autorun.
- 🔗 ADS Spy: Detects hidden Alternate Data Streams.
- 📈 TCPView: Monitors active network connections for malicious activity.
- 🔑 RegUnlocker: Unlocks registry keys that malware prevents access to.
Post-Analysis Tool UI Images
🚩 Important Best Practices
- Always verify unknown files via trusted services like VirusTotal.
- Perform manual file deletions in Safe Mode if malware files persist.
🎯 Basics Summary
Learning to analyze HijackThis! logs and understanding how to manually remove malware significantly improves your ability to secure and manage Windows systems effectively. Use this guide as a reference to confidently detect, analyze, and eliminate potential threats.
HijackThis!: Understanding F0, F1, F2, F3 Entries
HijackThis! logs can seem overwhelming due to their complexity, especially when interpreting entries labeled F0, F1, F2, and F3. These entries indicate programs loaded through traditional .ini files like system.ini and win.ini, or their modern registry equivalents.
🔍 F0 Entries (System.ini)
F0 entries correspond to the Shell statement located within the [Boot] section of the system.ini file. The Shell statement determines which graphical user interface Windows loads, typically Explorer.exe.
✅ Legitimate Example:
F0 - system.ini: Shell=Explorer.exe❌ Malicious Example:
F0 - system.ini: Shell=Explorer.exe badprogram.exeIn the malicious example, malware has modified the Shell statement to run an additional harmful executable at startup.
File Location:
C:\Windows\System.ini
While Windows ME and earlier versions use this file, Windows XP and later primarily rely on registry equivalents.
🔍 F1 Entries (Win.ini)
F1 entries represent legacy auto-run statements (Run= and Load=) within the win.ini file, historically used in Windows 3.1, 95, 98, and ME to execute programs automatically at startup.
❌ Malicious Examples:
F1 - win.ini: load=bad.pif
F1 - win.ini: run=evil.pifModern Windows versions (XP and newer) typically do not use win.ini for program execution, so encountering these entries on newer systems strongly indicates malicious activity.
File Location:
C:\Windows\Win.ini
🔍 F2 Entries (Registry Equivalent of F0 & F1)
F2 entries are the modern registry counterparts to F0 and F1 entries, specifically for Windows NT-based systems like XP, 2000, and later. These entries exist due to the IniFileMapping feature.
HijackThis! highlights these entries only if it detects potentially malicious or unusual modifications to critical registry keys:
HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\UserinitHKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell
❌ Malicious Examples:
F2 - REG:system.ini: UserInit=userinit.exe,nddeagnt.exe
F2 - REG:system.ini: Shell=explorer.exe beta.exe- UserInit: Determines the program running after user login. The legitimate default is:
C:\Windows\System32\userinit.exe,Code language: CSS (css)Any additional programs listed (like malware.exe) indicate potential infections.
- Shell: Usually loads Windows GUI (Explorer.exe). Additional executables alongside it (such as beta.exe) are suspicious.
⚠️ Warning: F2 entries often indicate infections. Thoroughly research unfamiliar values.
🔍 F3 Entries (Registry – User-Specific Settings)
F3 entries resemble F2 entries but specifically pertain to user-specific startup configurations in the registry:
HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows\loadHKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows\run
❌ Malicious Examples:
F3 - REG:win.ini: load=chocolate.exe
F3 - REG:win.ini: run=beer.exeThese registry entries trigger program execution on startup specifically for the logged-in user. Unknown entries should be carefully reviewed.
🛠 How to Analyze and Fix F0–F3 Entries
✔️ For F0 Entries:
- Safe if Shell only lists
Explorer.exe. - Investigate and remove additional unknown programs.
✔️ For F1 Entries:
- Entries on modern Windows systems are suspicious.
- Always verify unknown entries through web searches.
✔️ For F2 Entries:
- Safe if
UserInitonly listsuserinit.exe. - Safe if
Shellonly listsexplorer.exe. - Any additional entries require thorough investigation.
✔️ For F3 Entries:
- Investigate and remove unknown or suspicious user-specific startup entries.
⚠️ Important Notes
- HijackThis! removes registry references but does not delete associated files. Manual file deletion is required for full cleanup.
- Verify suspicious entries with VirusTotal or reputable antivirus programs.
🧰 Best Practices for Removal
- Always research entries before removal.
- Delete associated files in Safe Mode for safety.
- Use additional malware tools like Malwarebytes, AdwCleaner, or the Farbar Recovery Scan Tool (FRST) for comprehensive cleanup.
📌 F0, F1, F2, F3 Entries Summary
Accurately interpreting F0, F1, F2, and F3 entries in HijackThis logs is essential for identifying malware that leverages Windows startup processes. Careful analysis, validation of unknown entries, and manual cleanup of files provide the most effective strategy to ensure complete malware removal and system security.
HijackThis!: Understanding N1, N2, N3, and N4 Entries
Understanding HijackThis entries can significantly aid your ability to identify and resolve malware infections. This article focuses on the N1, N2, N3, and N4 entries specifically associated with Netscape and Mozilla browsers. Although these browsers are less common today, recognizing and interpreting these entries can still be valuable for legacy systems or specific troubleshooting scenarios.
📂 Storage Location of N Entries
The entries labeled N1 through N4 relate to settings stored within the prefs.js file. These files are browser-specific and have the following standard locations:
- Mozilla Firefox:
C:\Documents and Settings\YourUserName\Application Data\Mozilla\Firefox\Profiles\[ProfileName]\prefs.js - Netscape 4:
DriveLetter:\Program Files\Netscape\Users\default\prefs.js
It’s crucial to know the exact location as malware often modifies these files directly to hijack your browser settings.
🛡️ Explanation of N1, N2, N3, N4 Entries
HijackThis categorizes these entries based on browser versions:
- N1 Entries: Netscape 4’s Startup and Default Search Pages.
- N2 Entries: Netscape 6’s Startup and Default Search Pages.
- N3 Entries: Netscape 7’s Startup and Default Search Pages.
- N4 Entries: Mozilla-based browsers’ (like Firefox) Startup and Default Search Pages.
🕸️ Example of an N Entry
A typical entry might look like this:
N1 - Netscape 4: user_pref("browser.startup.homepage", "http://malicious-site.com");
N4 - Mozilla: user_pref("browser.startup.homepage", "http://unwanted-homepage.com");Code language: JavaScript (javascript)If you see URLs that you don’t recognize, it’s likely a sign of a browser hijacking. Hijackers manipulate these entries to redirect users to malicious sites, capture sensitive data, or force unwanted ads and pop-ups.
⚠️ How to Analyze and Fix Suspicious N Entries
Step 1: Review HijackThis Logs
- Run HijackThis and inspect your log closely for N1–N4 entries.
- Identify unfamiliar URLs that you didn’t set yourself.
Step 2: Confirm the URLs
- Perform a quick web search to identify whether the suspicious URL is safe or malicious.
- Utilize online malware databases such as VirusTotal to verify these URLs.
Step 3: Fixing Entries via HijackThis
- Open HijackThis.
- Check the box next to the suspicious N entry.
- Click “Fix Checked” to remove the entry from your settings.
Step 4: Manual Correction (Advanced Users)
- Navigate directly to the relevant
prefs.jsfile:C:\Documents and Settings\YourUserName\Application Data\Mozilla\Firefox\Profiles\[ProfileName]\prefs.js - Open the file using a text editor (e.g., Notepad).
- Find and manually remove or correct the suspicious homepage/search settings.
- Save and close the file.
⚠️ Important Notes:
- HijackThis only removes registry or prefs.js file references. It doesn’t delete associated malware files.
- Manual file deletion may be required for complete malware removal.
🛠️ Recommended Practices
- Always backup your
prefs.jsfile before making manual changes. - Regularly update your antivirus and anti-malware software.
- If uncertain about removing specific entries, consult a cybersecurity expert.
- Use HijackThis alongside tools like Malwarebytes or FRST (Farbar Recovery Scan Tool) for comprehensive malware detection and removal.
📌 N1, N2, N3, N4 Entries Summary
Understanding N1–N4 entries is vital for identifying potential hijacks within Netscape and Mozilla browser settings. Although Netscape browsers are rarely used today, Mozilla Firefox remains prevalent, making awareness of these entries relevant.
Regularly inspecting and managing these entries ensures your browsing experience remains secure and free from unwanted hijacking attempts.
🚨 HijackThis!: Understanding R0, R1, R2, and R3 Entries
HijackThis (HJT) is a powerful diagnostic tool that identifies potentially unwanted changes in Internet Explorer and system settings caused by malware or user modifications. One of the most common types of infections detected by HijackThis involves R0, R1, R2, and R3 entries.
These entries pertain to Internet Explorer’s start page, search page, search hooks, and other related configurations. Many malware infections modify these settings to redirect users to malicious websites, change default search providers, or alter how the browser processes unformatted URLs.
This section explains what these entries mean, how to interpret them in a HijackThis log, and how to safely clean unwanted entries.
What Do R0, R1, R2, and R3 Entries Mean?
🔹 R0 Entries
These correspond to Internet Explorer’s Start Page and Search Assistant settings.
📌 Example:
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://malicious-site.comCode language: JavaScript (javascript)If you see an unknown website, this could indicate a browser hijack.
🔹 R1 Entries
These represent Internet Explorer’s Search Functions and other characteristics.
📌 Example:
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://search-hijacker.comCode language: JavaScript (javascript)If this is pointing to an unknown site, HijackThis can safely remove it.
🔹 R2 Entries
This entry type is not currently used in modern HijackThis logs.
🔹 R3 Entries
These represent URL Search Hooks. A URL Search Hook is a mechanism that interprets incomplete web addresses when typed into the browser address bar.
📌 Example:
R3 - URLSearchHook: (No Name) - {12345678-ABCD-1234-ABCD-123456789ABC} - C:\Program Files\Hijacker\Hijack.dllIf the hook leads to an unknown DLL file, it is often associated with browser hijackers or adware.
Sample HijackThis Log Entries
Below is a sample of R0, R1, and R3 entries you may find in a HijackThis log:
R1 - HKCU\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://default-homepage.com
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://malicious-hijack.com
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://search-hijacker.com
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://unwanted-search.com
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://malicious-search-engine.com
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://fake-startpage.com
R1 - HKLM\Software\Microsoft\Internet Explorer\Search,Default_Page_URL = http://dangerous-site.com
R1 - HKCU\Software\Microsoft\Internet Connection Wizard,ShellNext = http://suspicious-url.com
R3 - URLSearchHook: (No Name) - {ABC12345-DEF6-789A-BCDE-1234567890AB} - C:\Program Files\Spyware\spyhook.dllCode language: JavaScript (javascript)How to Identify and Remove Unwanted R0, R1, and R3 Entries
✅ Step 1: Check the URLs
- If you don’t recognize the websites listed in R0 or R1, Google them or check them on VirusTotal.
- Sites with pop-ups, redirects, or fake search results are likely malicious.
🧰 Step 2: Use HijackThis to Fix the Entries
- Open HijackThis.
- Run a scan.
- Locate suspicious R0, R1, or R3 entries.
- Check the boxes next to them.
- Click Fix Checked.
🗑️ Step 3: Manually Delete Associated Files
- If an R3 entry points to a DLL, HijackThis won’t delete the file.
- Navigate to the file location.
- Use Safe Mode or Unlocker to remove the file.
🔄 Step 4: Reset Internet Explorer Settings
- Go to Tools > Internet Options in IE.
- Change homepage URL to a known-safe site (e.g., https://www.google.com).
- Reset your search provider under the Search tab.
📌 R0, R1, R2, R3 Entries Summary
- R0 entries define the Start Page and Search Assistant in Internet Explorer. Strange or unfamiliar entries may indicate redirection to malicious websites.
- R1 entries control Search Page settings and other browser-specific functions. Often hijacked by adware or search toolbars.
- R2 entries were used in older versions of IE but are now obsolete.
- R3 entries indicate URL Search Hooks, which may contain DLL references. Unknown or unsigned DLLs can signal malware presence.
By carefully analyzing these entries in a HijackThis log, you can detect and clean unwanted browser hijacks, helping restore your system’s normal browsing behavior.
🔐 HijackThis!: Understanding O7–O15 Entries
🔧 O7 Entries – Regedit Disabled
These entries indicate whether access to the Windows Registry Editor (Regedit) has been disabled. This could be a legitimate setting in corporate environments—or the work of malware trying to prevent you from inspecting system configurations.
📍 Registry Key:
HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System✅ Example Entry:
O7 - HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System: DisableRegedit=1⚠️ Important:
- Many IT admins disable Regedit on purpose.
- Do not fix this entry without confirming the setting is not policy-enforced.
🖱️ O8 Entries – Extra Context Menu Items
These entries represent custom right-click context menu items in Internet Explorer. Malware might use these to run unwanted scripts or links.
📍 Registry Key:
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\MenuExt✅ Example Entry:
O8 - Extra context menu item: &Google Search - res://c:\windows\GoogleToolbar1.dll/cmsearch.htmlCode language: JavaScript (javascript)📝 Notes:
- Legit entries like Google Toolbar are fine.
- Malicious ones should be fixed and the file manually deleted in Safe Mode if needed.
🛠️ O9 Entries – Custom IE Toolbar Buttons
These entries refer to custom buttons or entries added to Internet Explorer’s toolbar or “Tools” menu.
📍 Registry Key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Extensions✅ Example Entry:
O9 - Extra Button: AIM (HKLM)💡 Tips:
- Research the source. Legitimate apps like CCleaner may add these.
- HijackThis removes registry entries only—delete associated files manually in Safe Mode.
🌐 O10 Entries – Winsock Layered Service Providers (LSPs)
Layered Service Providers are part of the Windows networking stack. Some malware uses LSPs to intercept or modify network traffic.
✅ Example Entry:
O10 - Broken Internet access because of LSP provider 'spsublsp.dll' missingCode language: JavaScript (javascript)⚠️ Caution:
- Editing LSP chains can break your internet.
- Use tools like LSPFix to correct or repair broken chains.
- Consult SystemLookup’s LSP list for known safe vs. malicious entries.
🧩 O11 Entries – IE Advanced Options Hijacks
These entries modify which advanced options appear in Internet Explorer’s settings.
📍 Registry Key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\AdvancedOptions✅ Example Entry:
O11 - Options group: [CommonName] CommonNameCode language: CSS (css)🔎 Quick Check:
- “CommonName” is associated with known spyware.
- Search unknown entries before removal.
📄 O12 Entries – Internet Explorer Plugins
These represent IE plugins—used for rendering PDFs, Flash, and more.
📍 Registry Key:
HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Plugins✅ Example Entry:
Plugin for .PDF: C:\Program Files\Internet Explorer\PLUGINS\nppdf32.dllCode language: CSS (css)💡 Tip:
- Research each DLL or plugin.
- HijackThis removes the registry link, but you should delete suspicious DLLs manually.
🌍 O13 Entries – Default Prefix Hijack
A dangerous category: these modify how IE handles non-prefixed URLs (like typing just google.com).
📍 Registry Key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\URL\DefaultPrefix✅ Example Entry:
O13 - WWW. Prefix: http://ehttp.cc/?Code language: JavaScript (javascript)🚨 Common Malware:
- CoolWebSearch (CWS) often abuses this setting.
🧽 Fix:
- Use CWShredder to clean CoolWebSearch infections.
🧼 O14 Entries – Hijacked Web Settings Reset File
O14 entries manipulate the IE reset defaults found in the iereset.inf file.
📍 File Path:
C:\Windows\inf\iereset.infCode language: CSS (css)✅ Example Entry:
O14 - IERESET.INF: START_PAGE_URL=http://www.searchalot.comCode language: JavaScript (javascript)🔎 Note:
- Malware changes this to reinstate hijacked homepages after resetting browser settings.
- Confirm if manufacturer altered it before removal.
🛡️ O15 Entries – Trusted Zone and Protocol Default Hijacks
These alter IE’s Trusted Zone, which allows reduced security restrictions for specific sites and IP ranges.
📍 Registry Keys for Domains & Ranges:
HKLM\...\ZoneMap\Domains
HKCU\...\ZoneMap\Domains
HKLM\...\ZoneMap\Ranges
HKCU\...\ZoneMap\Ranges✅ Malicious Examples:
O15 - Trusted Zone: http://www.malwaresite.com
O15 - Trusted IP range: 69.161.125.149 (HKLM)Code language: JavaScript (javascript)🔒 Advice:
- Remove any sites or IPs that aren’t from a trusted network or business.
📍 Protocol Defaults Registry Keys:
HKLM\...\ZoneMap\ProtocolDefaults
HKCU\...\ZoneMap\ProtocolDefaults✅ Example of Protocol Hijack:
O15 - ProtocolDefaults: 'http' protocol is in Trusted Zone, should be Internet Zone (HKLM)Code language: JavaScript (javascript)🧹 Fixing O15 Entries
- Use HijackThis to restore proper zone placement.
- Double-check ZoneMap entries before removal.
📌 O7–O15 Entries Summary
Understanding O7 through O15 entries in HijackThis logs is critical when diagnosing complex malware infections. These entries relate to browser plugins, system policy restrictions, and IE security zones—all common targets for hijackers.
🔍 Always cross-reference unknown entries, use Safe Mode for deletion when needed, and pair HijackThis with tools like CWShredder, LSPFix, or VirusTotal to fully clean up your system.
Removing these entries restores browser integrity, ensures proper system policies, and prevents scripts from running under weakened security contexts.
🔐 HijackThis!: Understanding O16–O22 Entries
O16 Entries – ActiveX Objects (Downloaded Program Files)
ActiveX controls are downloaded components used primarily by Internet Explorer to enable extended functionality on websites. HijackThis detects them under the O16 category.
📍 Storage Locations:
- Files:
C:\Windows\Downloaded Program Files\ - Registry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Code Store Database\Distribution Units\
✅ Example Legitimate Entry:
O16 - DPF: {11260943-421B-11D0-8EAC-0000C07D88CF} (iPix ActiveX Control) - http://www.ipix.com/download/ipixx.cabCode language: JavaScript (javascript)📅 Tips:
- Do not remove all O16 entries blindly.
- Verify the site and purpose of each control.
- If the file is malicious and HijackThis fails to delete it, use Safe Mode for manual removal.
O17 Entries – Lop.com and DNS Hijacks
The O17 section logs DNS-related hijacks. These entries often show modified NameServer settings that redirect all internet traffic through a rogue DNS server.
✅ Example Malicious Entry:
O17 - HKLM\System\CS1\Services\VxD\MSTCP: NameServer = 69.57.146.14,69.57.147.175🚨 Why It Matters:
- A DNS hijack can redirect every domain you visit to phishing or malware sites.
📑 How to Check:
- Use ARIN WHOIS to look up the DNS server IPs.
- If they’re untrusted, fix the entry in HijackThis and reset network settings.
O18 Entries – Extra Protocols and Protocol Hijackers
HijackThis uses the O18 section to list protocol handlers and filters. Hijackers exploit these to redirect or monitor your browsing behavior.
📅 Registry Locations:
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\PROTOCOLS\
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\PROTOCOLS\Handler
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\PROTOCOLS\Filter✅ Suspicious Example:
O18 - Protocol: relatedlinks - {5AB65DD4-01FB-44D5-9537-3767AB80F790} - C:\PROGRA~1\COMMON~1\MSIETS\msielink.dll🚨 Common Offenders:
- Lop.com
- Related Links
- CoolWebSearch
🛠️ Fix:
- HijackThis removes the registry pointer.
- You must manually delete the DLL file (in Safe Mode recommended).
O19 Entries – User Style Sheet Hijacks
O19 entries point to custom CSS files that override website appearance or behavior. Malware can abuse this to inject popups or hide warnings.
📍 Registry Key:
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Styles\: User Stylesheets✅ Malicious Example:
O19 - User style sheet: c:\WINDOWS\Java\my.cssCode language: CSS (css)🔎 Fixing It:
- HijackThis removes the registry reference.
- Manually delete the CSS file after reboot.
O20 Entries – AppInit_DLLs and Winlogon Notify Hijacks
AppInit_DLLs:
These DLLs are injected into every GUI application and run whenever user32.dll loads—making them a favorite for stealthy malware.
📍 Registry Key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\AppInit_DLLs✅ Example:
O20 - AppInit_DLLs: C:\WINDOWS\System32\winifhi.dllCode language: CSS (css)Winlogon Notify:
These entries trigger DLLs to run at login. They provide persistence and are often difficult to detect.
📍 Registry Key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify✅ Example:
O20 - Winlogon Notify: Extensions - C:\WINDOWS\system32\i042laho1d4c.dllCode language: CSS (css)🚨 Fixing O20 Entries:
- HijackThis removes the registry value only.
- Delete the DLL manually in Safe Mode.
O21 Entries – ShellServiceObjectDelayLoad (SSODL)
SSODLs are DLLs that load automatically with Explorer.exe. While some are legitimate, malware often abuses this feature.
📍 Registry Key:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\ShellServiceObjectDelayLoad✅ Example:
O21 - SSODL: System - {3CE8EED5-112D-4E37-B671-74326D12971E} - C:\WINDOWS\system32\system32.dll🚫 Note:
- HijackThis doesn’t delete the actual file.
- Use Safe Mode to delete the DLL manually.
O22 Entries – SharedTaskScheduler Hijacks
O22 entries specify background tasks loaded by Windows Explorer. Malware often uses this to create fake security alerts or toolbars.
📍 Registry Key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SharedTaskScheduler✅ Example:
O22 - SharedTaskScheduler: (no name) - {3F143C3A-1457-6CCA-03A7-7AA23B61E40F} - c:\windows\system32\mtwirl32.dll🔧 Cleanup Instructions:
- HijackThis removes the registry entry.
- You must delete the file manually, especially if used by SmitFraud or similar.
📊 O16–O22 Entries Summary
The O16–O22 sections cover some of the most dangerous malware persistence mechanisms in HijackThis logs. From ActiveX to protocol hijackers and DLL-based persistence, these entries often fly under the radar unless examined closely.
🔎 Always verify unknown DLLs, CLSIDs, or IP addresses. Use VirusTotal, WHOIS, and Safe Mode to clean up what HijackThis flags.
👁🔍 Pair HijackThis with modern tools like:
- FRST (Farbar Recovery Scan Tool)
- LSPFix
- Autoruns
- AdwCleaner
Remember: HijackThis only removes registry references—you must hunt down and eliminate the actual files manually to stop the infection completely.
HijackThis!: Understanding O23 Entries – Malware Installed as a Service
Malware as a Service: The Hidden Threat
The O23 section in HijackThis! targets Windows Services — background processes that load automatically at system boot. While services are critical for system functionality (like networking, antivirus, or printing), malware authors have learned to exploit them.
🛑 Why it matters: Malware services launch before antivirus tools, hide from task managers, and reinstall other infections if not removed completely.
How Services Work (and How Malware Uses Them)
Services run independently of logged-in users and operate system-wide. They’re ideal for persistence, which makes them a favored method for advanced malware.
✅ Common legitimate uses:
- Windows components (e.g., Windows Update, SecurityHealthService)
- Antivirus tools (e.g., Malwarebytes, Windows Defender)
- Hardware support (e.g., Realtek Audio, NVIDIA)
❌ Malicious uses:
- Browser hijackers
- Keyloggers
- Backdoors
- Downloaders that fetch more malware
HijackThis logs these as O23 entries.
How HijackThis Detects Services
By default, HijackThis hides known-good services. To reveal everything:
🧪 Run HijackThis with the **/ihatewhitelists** flag.
This exposes all services, both legitimate and unknown, giving analysts a full view.
Examples of O23 Entries
✅ Legitimate Service Example:
O23 - Service: AVG7 Alert Manager Server (Avg7Alrt) - GRISOFT, s.r.o. - C:\PROGRA~1\Grisoft\AVGFRE~1\avgamsvr.exeCode language: CSS (css)🟢 Description: Standard service from AVG antivirus.
❌ Malware Example – Home Search Assistant:
O23 - Service: Workstation NetLogon Service - Unknown - C:\WINDOWS\system32\crxu.exeCode language: CSS (css)🔴 Red flags:
- Unknown publisher
- Suspicious file in
system32 - Impersonates a Windows component
❌ Adware Examples – Bargain Buddy:
O23 - Service: ZESOFT - Unknown - C:\WINDOWS\zeta.exe
O23 - Service: ISEXEng - Unknown - C:\WINDOWS\System32\angelex.exeCode language: CSS (css)🟠 Adware components that hijack search settings and inject ads.
What Fixing O23 Entries Does
When you click Fix Checked in HijackThis for an O23 entry:
✅ It:
- Disables the service from starting at boot
- Stops the service (if running)
- Prompts a reboot
🚫 It does not:
- Delete the service’s registry key
- Remove the actual malware file
🔧 For full removal, manual cleanup is needed.
How to Manually Delete a Malicious Service
You have three options to remove rogue services:
🛠️ Method 1: Use Command Prompt
- Open Command Prompt as Administrator
- Run:
sc delete ServiceNameCode language: JavaScript (javascript)🔍 Replace ServiceName with the service’s internal name (in parentheses).
Example:
sc delete ISEXEngCode language: JavaScript (javascript)📁 Method 2: Use a Registry File
Create a .reg file like this:
Windows Registry Editor Version 5.00
[-HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_ISEXENG]
[-HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\ISEXEng]
[-HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum\Root\LEGACY_ISEXENG]
[-HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\ISEXEng]
[-HKEY_LOCAL_MACHINE\SYSTEM\ControlSet003\Enum\Root\LEGACY_ISEXENG]
[-HKEY_LOCAL_MACHINE\SYSTEM\ControlSet003\Services\ISEXEng]Code language: CSS (css)💾 Save as RemoveService.reg, run it, and reboot.
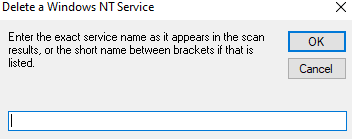
🔧 Method 3: Use HijackThis Built-in Tool
- Launch HijackThis
- Go to Config > Misc Tools
- Select Delete an NT service
- Enter the service name from the O23 entry
- Confirm and reboot
👍 This is often the easiest method for beginners.
How to Spot Malicious Services
Use these signs to determine if an O23 service is suspicious:
✅ Check the Name
- Real:
WinDefend,Spooler,W32Time - Fake:
NetDDEsrv,ZESOFT,ISEXEng
✅ Check the Publisher
- Trusted: Microsoft, Intel, Malwarebytes
- Unknown = red flag
✅ Check the Location
- Safe:
C:\Windows\System32\ - Suspicious:
C:\Temp\,C:\Users\[user]\AppData\
✅ Use Online Scanners
⚙️ A Note on ELAM (Early Launch Anti-Malware)
Modern antivirus programs use ELAM drivers that launch before third-party software. While this helps detect rootkits, it’s worth noting:
🛡️ ELAM only works after bootloaders execute. ❌ ELAM does not prevent bootkits, which run before ELAM loads.
So while ELAM improves startup security, it doesn’t replace manual investigation of persistent malware like those in O23 entries.
🚀 O23 Entries Summary
The O23 section is one of the most powerful areas of a HijackThis log — and one of the most abused by malware.
🔍 Always:
- Compare service names to known Windows defaults
- Research file paths and publishers
- Pair HijackThis with FRST, Autoruns, and VirusTotal
⚠️ Remember: HijackThis only removes registry entries — not the malware files. Deletion must be done manually or with other tools.
Stay sharp, stay safe, and always dig deeper when investigating services!
🧹 HijackThis!: Understanding NT Services: Stopping and Removing Malicious Ones
🚨 Why Malicious Services Matter
Malicious NT Services are like digital parasites — burrowed deep into your system, starting at boot, running in the background, and often immune to normal removal techniques.
These services appear in O23 entries within a HijackThis log. While many services are essential and legitimate, attackers often disguise malware as background system services to achieve persistence, stealth, and control.
If you’ve spotted a suspicious service in your scan, this guide will walk you through two powerful ways to shut it down for good.
🔍 Spotting a Suspicious Service
Here’s an example of a malicious NT service entry you might see in a HijackThis log:
plaintextCopyEditO23 - Service: NetDDE Server (NetDDEsrv) - Unknown owner - C:\WINDOWS\System32\netddesrv.exe
🛑 Warning signs:
- “Unknown owner” — no verified publisher
- Odd file paths or file names (like netddesrv.exe)
- Masquerading as legitimate Windows services (e.g., NetDDE is obsolete)
If it looks shady, it probably is. Let’s remove it.
🧰 Method 1: Remove a Service Using a Batch Script (Automated)
You can automate service removal using a simple batch file.
📄 Steps:
- Open Notepad.
- Paste the following code:
batchCopyEdit@echo off
sc stop <insert service name 1>
sc stop <insert service name 2>
sc delete <insert service name 1>
sc delete <insert service name 2>
del FixServices.bat
- Replace the placeholders with your actual service names.
Example:
batchCopyEdit@echo off
sc stop NetDDEsrv
sc delete NetDDEsrv
del FixServices.bat
- Save it as:
📁FixServices.bat(Set “Save as type” to All Files) - Run the batch file by double-clicking it.
🔁 A black command prompt window will briefly appear and close — that’s normal.
💬 Tip: After running, right-click and delete the batch file manually.
⚠️ Note: Some antivirus software may flag this file as suspicious. If you’re confident in the file, allow it to run.
🧑🔧 Method 2: Remove a Service Using HijackThis (Manual)
HijackThis includes a tool for removing NT Services. Here’s how to use it:
🛠️ Step-by-Step:
- Open HijackThis.
- Click “Config…” in the lower-right.
- Go to the “Misc Tools” tab.
- Select “Delete an NT Service”.
- Enter the service name from your O23 entry (from the parentheses).
Example: If you see:
plaintextCopyEditO23 - Service: NetDDE Server (NetDDEsrv) - Unknown owner - C:\WINDOWS\System32\netddesrv.exe
You’ll enter:
nginxCopyEditNetDDEsrv
- Click OK and reboot your PC.
✅ This method works well for those comfortable using HijackThis directly.
🧼 Final Tip: Don’t Just Stop the Service — Delete the File
Stopping and unregistering the service does not delete the malware file. After removing the service:
- Navigate to the file location (in the example above:
C:\WINDOWS\System32\netddesrv.exe) - Reboot into Safe Mode if needed
- Delete the executable manually
For extra caution, upload it to:
📌 If the file can’t be deleted:
- Use tools like Unlocker, Process Explorer, or boot into Safe Mode with Command Prompt.
✅ NT Services Summary
HijackThis provides visibility into deep system behavior — especially dangerous NT services hiding as legitimate processes. By learning to identify, stop, and delete them, you build confidence and control over your system’s health.
🧠 Key takeaways:
- Check the O23 section of your logs.
- Confirm file location, publisher, and service name.
- Use batch scripts or HijackThis tools to remove malicious entries.
- Always delete the malware file manually.
With these steps, you’ll be better equipped to defend against deeply embedded infections.
🧠 Final Conclusion: Mastering HijackThis! for Malware Defense
HijackThis! remains one of the most granular, hands-on tools available for identifying and dissecting malware infections that other scanners might overlook. From deeply embedded NT Services to legacy .ini entries, obscure browser hijacks, protocol handlers, and DNS redirections—this guide has walked you through the hidden layers where threats often take root.
The strength of HijackThis! lies not in flashy automation, but in transparency. It shows you everything—the good, the bad, and the suspicious—leaving the final judgment to you. With the right understanding of each log category (from R0–R3, F0–F3, N1–N4, O1–O23), you can pinpoint where malicious actors have burrowed into your system, and remove them piece by piece.
But with that power comes responsibility: HijackThis! doesn’t delete files, repair damage, or restore defaults. It gives you the map. You take the action.
✅ Use it in combination with tools like VirusTotal, Autoruns, CWShredder, LSPFix, and FRST.
✅ Back up before making changes.
✅ Always investigate unfamiliar entries.
✅ Use Safe Mode when deleting persistent malware files.
Whether you’re cleaning an infected machine or performing proactive maintenance, this guide equips you with the foundation needed to confidently dissect, diagnose, and defuse complex threats.
The more you understand the log, the stronger your defense becomes.
The following articles from sm-u.com are resources to further your virus and malware analysis knowledge:
- [Malware & Virus Analysis Resources (Tool List)]
A constantly updated list of tools, utilities, and platforms for malware analysis. - [Rootkits 101: Detecting and Removing Rootkits]
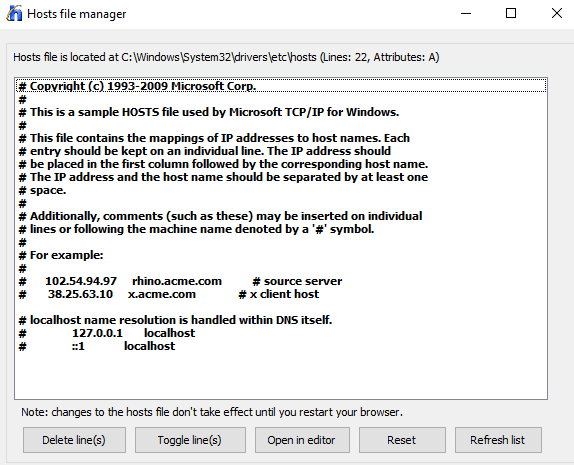
Understand how rootkits work, how they hide, and how to effectively root them out. - [How to Fix a HOSTS File Infection]
A deep dive into HOSTS file abuse by malware and how to safely reset and lock it down. - [Setting Up a Virtual Machine for Malware Testing & Analysis]
Build a safe environment to analyze suspicious files and system behaviors without risk. - [File-Infector Virus 101: What It Is & How to Remove It]
Learn to detect, isolate, and clean viruses that attach themselves to legitimate executables. - [Free Virus and Malware Removal Guide]
A comprehensive beginner-to-advanced disinfection walk-through using trusted free tools.
Whether you’re cleaning an infected system, dissecting malware behavior, or learning to harden your defenses — combining HijackThis! with the resources above creates a solid, modern malware-fighting toolkit.

