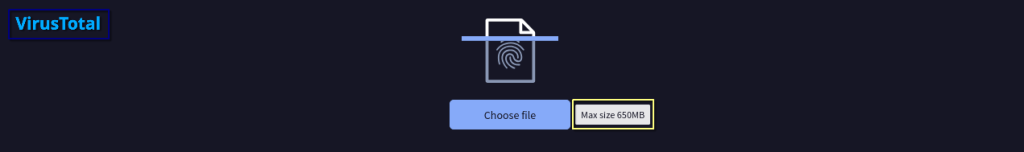
In the world of malware analysis, it’s not uncommon to run into files that are deceptively large. Why? Because attackers use a technique called file padding to sneak past detection tools. When these oversized files bypass platforms like VirusTotal—which has a 650MB upload limit—it’s easy to see how this tactic gives attackers an edge.
But with proper file padding removal, you can level the playing field. Let’s break it down.
🔍 What Is File Padding?
To start, file padding refers to the process of injecting additional, non-functional bytes (often just 00s) into a file. These bytes serve no real purpose other than to alter the file’s size or structure.
This method is commonly used by threat actors—and occasionally by security pros—to:
- Evade Detection: Padding changes file structure, confusing antivirus and automated analysis tools.
- Obfuscate Code: It buries the actual logic under layers of useless data, slowing down reverse engineering.
- Exploit Vulnerabilities: Carefully placed padding can even help trigger buffer overflows.
- Bypass Size Filters: Enlarging a file might allow it to sneak past upload or scanning restrictions.
🚧 Understanding the Drawbacks
However, it’s important to recognize that this method isn’t without its flaws.
For one, modern security tools are increasingly capable of detecting abnormal file structures, including excessive padding. Also:
- Performance Lag: Padded files become bloated, affecting system performance.
- Manual Review Still Wins: Skilled analysts can often see through padding tricks.
- Predictable Patterns: Detection algorithms can flag repeated or suspicious padding behaviors.
This is where file padding removal becomes a critical step during malware triage.
🧠 File Padding in Malware Analysis
So how exactly is padding used in real-world malware? Let’s explore:
- Signature Evasion: Padding can blur known byte patterns, weakening signature-based detection.
- Static Analysis Disruption: It may mislead tools into misinterpreting control flow.
- Code Concealment: Redundant or junk data makes it harder to find the real malicious payload.
- Sandbox Manipulation: Malware might detect file structure changes and adjust its behavior to avoid automated analysis.
- Overwhelming Automation: Analysis tools waste time parsing irrelevant data—slowing down incident response.
To cut through the noise, file padding removal helps isolate the meaningful parts of the file, accelerating deeper inspection.
💡 Case Study: Real-World File Padding
Let’s take a look at a concrete example. In a recent forum post, someone shared a tool called “Free Ultimate Proxy Checker” by Toxic Coder. It was advertised as a simple Crypto Checker.
But something was off—the file size was 762MB, which is unusually large for such a lightweight utility.
🔧 Using GHex for File Padding Removal
To investigate, we opened the file in GHex, a hex editor. Right away, we noticed that the file was front-loaded with 00 bytes—classic padding.

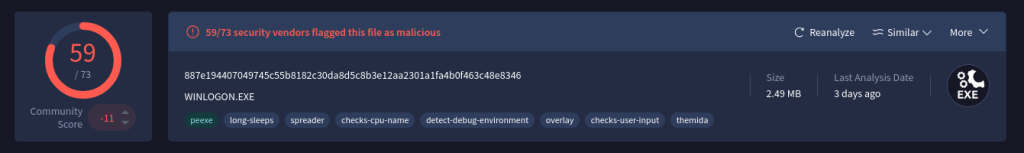
After applying file padding removal and stripping out the non-functional bytes, the file’s size dropped to 2.6MB.
That’s a file we can now upload to VirusTotal.
🎯 Result: VirusTotal scan link
✅ Final Thoughts
While not the most common evasion tactic today, file padding remains a clever trick—often targeting users who are technical enough to upload a suspicious file to VirusTotal, but not yet familiar with evasion techniques like padding. Recognizing and applying file padding removal can save you time, reduce confusion, and expose the real threat behind the noise.
Cleaning padded files is a critical early step, especially if you’re preparing for deeper malware analysis or reverse engineering. By identifying and removing padding, you restore clarity and increase the effectiveness of your tools.
🔗 Related Reads to Level Up Your Malware Analysis Skills
If you’re serious about improving your threat-hunting and malware triage skills, these guides will help you take the next step:
- 🧼 Free Virus and Malware Removal Guide – A beginner-friendly walkthrough for eliminating threats from infected systems.
- 🧬 File Infector Viruses 101: How to Identify and Remove Them – Learn how file infectors behave and how to detect their presence, even when they try to hide inside padded files.
- 🧪 Setting Up a Virtual Machine for Malware Testing and Analysis – Discover how to safely build your own analysis lab for hands-on malware investigation.
With techniques like file padding removal in your toolkit, and the right resources by your side, you’re already one step ahead in the fight against modern malware.
Want more analysis tips? Stay tuned for our full VirusTotal guide—coming soon.

