🦠 Understanding File Infectors: What They Are and How They Work
A file infector virus is a dangerous type of malware that injects malicious code into executable files. Once infected, these files can no longer be trusted—they may appear normal, but they’re now carriers of malware that can corrupt key system files and spread rapidly across devices.
🔹 When you run an infected file, the virus activates and begins infecting others.
🔹 These threats often target file types like .EXE, .COM, .SCR, .HTM, .HTML, .XML, .ZIP, and .RAR.
🔹 They typically hide in memory, waiting for a specific event to trigger additional infections.
🔹 A file infector virus can spread through USB drives, malicious websites, email attachments, and network file sharing.
💡 Important: Many modern file infectors are so persistent that removing them is nearly impossible—a full system reformat is often required.
🛠️ How File Infectors Behave
Here are some telltale behaviors that most file infectors share:
- They load into memory when executed and begin spreading to other executables.
- The original file stays dormant while the virus runs first in the background.
- A separate copy of the virus is often created to ensure reinfection later.
- The host program is eventually executed, which hides the infection from the user.
- Each time a user opens a new app, the virus finds new targets to infect.
This makes a file infector virus particularly dangerous—it’s stealthy, fast-spreading, and extremely difficult to detect without specialized tools.
🚨 Dangerous Polymorphic File Infectors
Polymorphic viruses mutate their code with every new infection, making them extremely hard to detect using traditional antivirus methods. Below are some of the most well-known polymorphic file infectors:
🦠 Virut
One of the most aggressive and persistent file infectors in the wild.
✔ Targets: .EXE, .SCR
✔ Spreads via: Internet downloads, file-sharing platforms
✔ Features: Backdoor access via IRC botnets, opens Port 65520
✔ Backdoor Domain: bproxim.ircgalaxy.pl
🛑 Symptoms:
- Problems with internet connectivity
- Antivirus software fails to run or update
- Frequent crashes and corrupt files
❌ Removal:
Virut cannot be cleaned—you’ll need to wipe your system completely. Check the following files for infection:
C:\Windows\System32\userinit.exe
C:\Windows\explorer.exe
C:\Windows\System32\svchost.exe🦠 Sality
A network-savvy file infector virus that disables security tools and evades detection.
✔ Targets: Core system files and antivirus software
✔ Spreads via: USB drives, P2P networks, shared folders
✔ Features: Uses rootkit techniques to remain hidden
🛑 Symptoms:
- Slow system performance or crashes
- Antivirus tools stop working or disappear
- Elevated CPU usage from malicious processes
❌ Removal:
Like Virut, Sality requires a full system reformat. Some commonly infected files include:
C:\Windows\System32\syslib32.dll
C:\Windows\System32\oledsp32.dll
C:\Windows\System32\olemdb32.dll
C:\Windows\System32\wcimgr32.dll
C:\Windows\System32\wmimgr32.dll🦠 Ramnit
A hybrid malware that functions as a file infector virus, worm, and backdoor.
✔ Targets: .EXE, .DLL, .HTML files
✔ Spreads via: USB devices, compromised websites, file-sharing
✔ Features: Steals browser cookies and banking credentials
🛑 Symptoms:
- Browser redirects and strange activity
- Suspicious processes in Task Manager
- Random file deletion or modification
❌ Removal:
Not cleanable. A full format and OS reinstall is necessary.
🦠 Expiro
A stealthy, modular virus that infects every executable file it finds.
✔ Targets: .EXE, .DLL
✔ Spreads via: Infected downloads and network shares
✔ Features: Harvests stored credentials and browser data
🛑 Symptoms:
- Missing files or corrupted data
- Infections in system files like
explorer.exeorsvchost.exe - Sluggish system behavior
❌ Removal:
Only safe solution is a full system wipe.
🚀 Other Noteworthy File Infectors
Here are some additional threats worth knowing about:
- Xpaj – Advanced rootkit with polymorphic infection strategies
- ZMist (Zombie Mist) – First known metamorphic virus, fully rewrites itself
- Parite – Spread via networks, especially SMB shares
- Sasfis – File infector that also drops trojans and spyware
- Delf – Infects executables and scripts like
.VBS,.BAT - Phorpiex – Combines file infection with ransomware and worm-like behavior
❌ Can File Infectors Be Removed?
🚨 Short answer: No.
Due to their aggressive and stealthy behavior, a file infector virus is almost impossible to clean reliably. The only guaranteed solution is to start fresh.
✅ What You Should Do (;tldr)(explained in detail below):
- Backup important files (non-executables only, like photos/documents)
- Reformat your hard drive and reinstall Windows
- Change all your passwords, especially for online accounts and banking
- Check BIOS/UEFI firmware, though rare, some viruses can persist there
- Reinstall only from trusted software sources
🖥️ How to Format and Reinstall Windows 10/11 (Step-by-Step)
If your system is infected with a file infector virus and cleaning isn’t an option, a full format and reinstall of Windows 10 is the safest route. Here’s how to do it:
🔧 What You’ll Need:
- A USB flash drive (at least 8GB)
- Another working computer to create installation media
- Your Windows 10 product key (optional, usually activated automatically)
📝 Step 1: Back Up Your Data
Before you format your drive, back up only non-executable files like:
- Photos, videos, documents
- Emails or browser bookmarks
- Save files or work projects
⚠️ Do NOT back up .EXE, .DLL, or .SCR files—these could carry the virus.
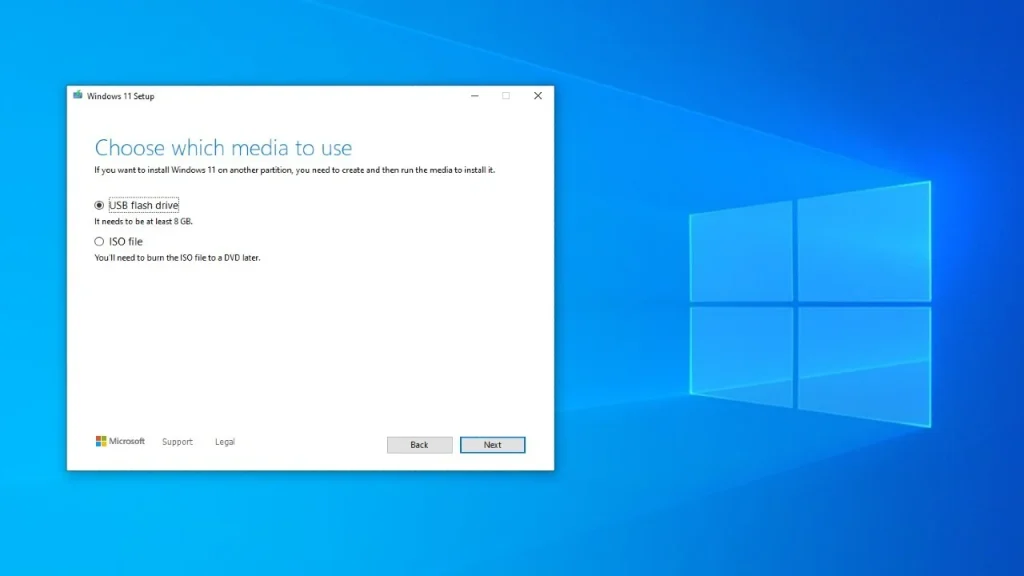
💾 Step 2: Create a Bootable USB Installer
- Go to the official Microsoft Windows 10 download page.
- Download the Media Creation Tool.
- Run the tool and choose “Create installation media (USB flash drive)”.
- Select your language, edition, and architecture.
- Insert your USB drive and follow the prompts to make it bootable.
🧹 Step 3: Boot from the USB & Format
- Insert the USB drive into the infected PC.
- Restart your computer and boot from the USB:
- Press the appropriate key during startup (usually
F2,F12,DEL, orESC) to open boot options.
- Press the appropriate key during startup (usually
- Select the USB drive and press
Enter.
💻 Step 4: Reinstall Windows 10/11
- Once the installer loads, select your language and click Next.
- Click Install Now.
- When prompted, select “Custom: Install Windows only (advanced)”.
- On the next screen, you’ll see a list of partitions. Select your main drive (usually Drive 0) and click Delete for each partition.
- After all partitions are deleted, select the unallocated space and click Next.
Windows will now begin the installation process.
Want help recovering from an infection?
🔧 Although there is no way besides a full system format to ensure removal of a file infector virus, check out this free virus and malware removal guide to safely restore your system and eliminate any other more basic lingering threats.