DLL sideloading is a sophisticated technique used by attackers to inject malicious code into legitimate processes. This guide covers what DLL sideloading is, how attackers use it, how to detect it using DLLHound, and how to prevent and remove it effectively. Additionally, we explain how thick clients relate to this issue and provide proactive strategies for IT and security professionals.
🧩 What Is DLL Sideloading?
DLL sideloading exploits how Windows searches for Dynamic Link Library (DLL) files when an application is launched. When an executable calls a DLL without specifying its full path, Windows uses a pre-defined search order to locate it. If a malicious DLL with the same name is placed earlier in the search path, the system might load it, granting the attacker code execution—often with elevated privileges.
There are two primary attack types:
Passive Exploitation
A trusted, digitally signed executable is placed alongside a malicious DLL with the same name as a legitimate dependency. When the executable runs, it loads the malicious DLL.
Active Exploitation
The attacker targets an already-installed application that searches for missing or incorrectly referenced DLLs. The attacker places a malicious DLL in a directory that appears earlier in the DLL search order. If the vulnerable app has administrative permissions, the malicious code inherits the same privileges.
🖥️ What Is DLLHound?
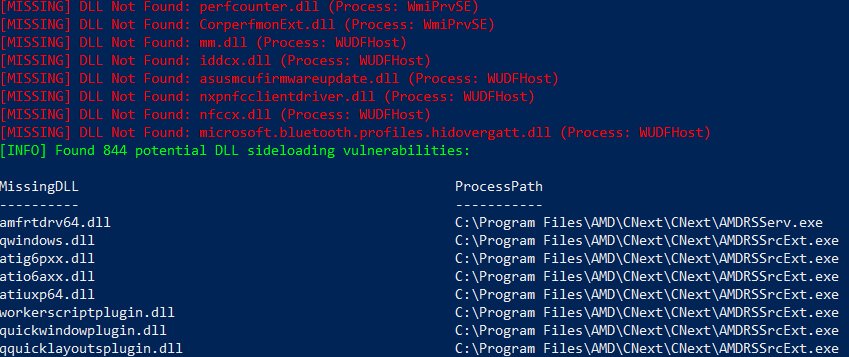
DLLHound is a lightweight PowerShell-based tool that scans your Windows system for DLL sideloading vulnerabilities. It identifies unresolved or missing DLLs across running processes, which can be exploited via DLL sideloading.
🔧 Key Features
- Dynamic Process Analysis: Identifies missing or unresolved DLLs across all running processes.
- Customizable Search Paths: Allows tailored scans by adding specific directories to the DLL search path.
- Custom Scan Settings: Define executable size limits and DLL dependency caps.
- Formatted Output: Results are displayed in a clean terminal table.
- CSV Export: Option to save output to a CSV file for analysis.
- Quick Access: Easily open the directory of flagged executables.
⚙️ How to Use DLLHound
Installation & Setup
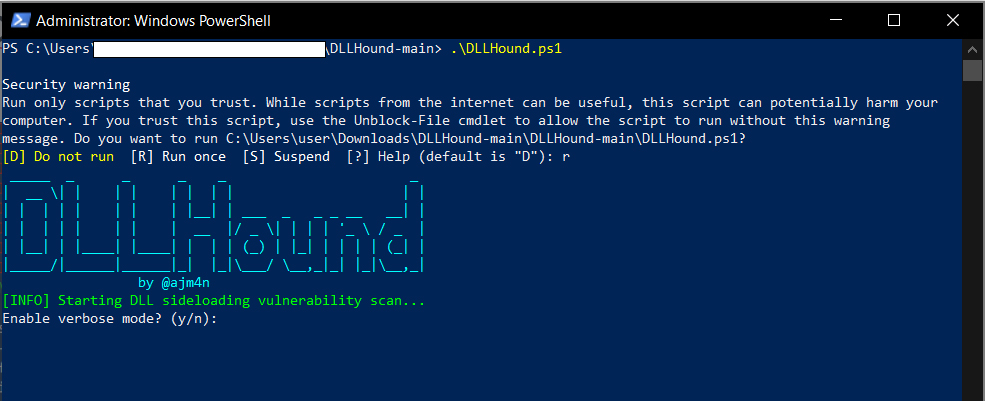
- Clone or download DLLHound from GitHub.
- Open PowerShell as Administrator.
- Navigate to the DLLHound directory.
Run the Tool
.\DLLHound.ps1Code language: CSS (css)⚠️ Execution Policy Error Fix
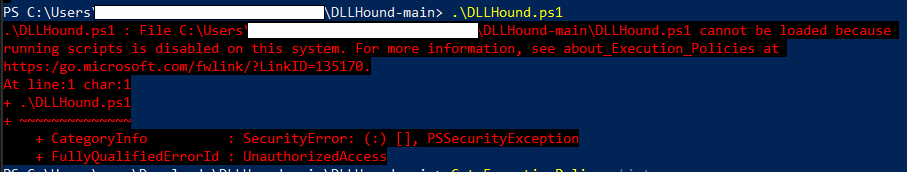
If you get an error stating that script execution is disabled:
Set-ExecutionPolicy -ExecutionPolicy UnrestrictedCode language: JavaScript (javascript)After running the script, reset your policy for security:
Set-ExecutionPolicy -ExecutionPolicy RestrictedCode language: JavaScript (javascript)Learn more: about_Execution_Policies
🛡️ Detection and Prevention of DLL Sideloading
Detection Techniques
- Monitor Process Behavior: Use behavioral analytics to detect abnormal DLL loads.
- Network Monitoring: Tools like ExeonTrace detect anomalies in flow and packet data.
- Use Process Monitor: Microsoft’s Process Monitor tracks how DLLs are loaded and reveals unsafe load paths.
- Compare DLL Load Order: Check for inconsistencies between expected and actual load paths.
Prevention Tips
- Use Fully Qualified Paths: Always specify the full path when calling DLLs in your code.
- SetDllDirectory(“”): Remove the Current Working Directory (CWD) from the search path.
- Use Safe DLL Search Mode: Use
SetSearchPathMode(BASE_SEARCH_PATH_ENABLE_SAFE_SEARCHMODE | BASE_SEARCH_PATH_PERMANENT). - Apply Application Whitelisting: Ensure only verified applications can run.
- Patch Vulnerable Software: Keep software updated and remove legacy binaries vulnerable to hijacking.
🔨 Rebuild the Environment with Secure Practices
After a DLL sideloading attack is detected and removed, it’s critical to harden your environment to prevent future exploits.
🛠️ Rebuilding Securely
- Code Review: Conduct a comprehensive audit of all application source code. Ensure every call to
LoadLibraryor related functions uses fully qualified paths. Avoid usingSearchPath()and never load DLLs using CWD. - Patching and Updates: Regularly update operating systems, applications, and third-party libraries. Many DLL hijacking issues stem from outdated or unsupported software.
- Enforce Developer Guidelines: Provide developers with Microsoft’s guidance on secure DLL loading. Discourage use of weak patterns such as loading DLLs based on current directories or environment variables.
- Remove Deprecated Applications: Audit and eliminate legacy or unsupported applications that may not adhere to secure DLL loading practices.
- Automate Security Testing: Use static and dynamic analysis tools in CI/CD pipelines to identify insecure code patterns before deployment.
- Zero Trust Principles: Enforce least privilege access, segment the network, and verify every device or user trying to access resources.
By rebuilding your environment with these practices, you reduce the likelihood of future sideloading or preloading attacks.
What Are Thick and Thin Clients?
In computing, thick clients (also known as fat clients) are devices that have most of their resources—such as storage, applications, and processing power—installed and available locally. These devices, typically desktop PCs or laptops, function independently even without a continuous connection to a central server. They excel in performance, allow users to work offline, and offer greater customization and flexibility. Businesses often deploy thick clients to empower employees with robust computing capabilities, especially in hybrid or work-from-home environments.
In contrast, thin clients depend heavily on a central server to perform most computing tasks. They have minimal local resources and typically access applications and storage hosted elsewhere. While thin clients are easier to manage, require fewer updates, and are often more secure due to centralized control, they rely on consistent network availability. This makes them ideal for controlled environments like kiosks, call centers, or terminals with dedicated usage.
🖥️ Thick vs. Thin Clients and DLL Sideloading
Thick Clients
A thick client is a workstation with locally installed OS, apps, and processing power. It doesn’t rely on a continuous server connection, making it more susceptible to DLL sideloading if not properly secured.
Pros:
- Full offline functionality
- Lower reliance on server performance
- User-level customization
Cons:
- Greater attack surface due to locally stored DLLs
- Requires user responsibility for updates and patching
Thin Clients
In contrast, thin clients rely heavily on centralized servers and have minimal local resources. They’re easier to control centrally but limit user flexibility.
Pros:
- Easier to secure and manage
- Lower hardware costs
Cons:
- Heavily dependent on network availability
- Limited local processing power
Relevance to DLL Sideloading
Thick clients are a common attack surface for DLL sideloading because they:
- Store more binaries and applications locally
- Are less likely to be monitored in real time
- Can run legacy or unsigned applications
Tools like DLLHound are particularly useful for analyzing thick clients in red team or pentest scenarios.
RMM vs. MDM and How They Relate to Sideloading
While RMM (Remote Monitoring & Management) tools are more focused on managing servers, desktops, and applications, MDM (Mobile Device Management) handles smartphones and tablets. For full endpoint protection, both should be deployed, especially to defend against sideloading attacks across different device types. You can find a list of the top 10 RMM and MDM platforms of 2025 on this site.
✅ Conclusion
DLL sideloading continues to be a favored technique for attackers due to its stealth and persistence capabilities. Tools like DLLHound help defenders scan and detect vulnerable systems quickly. Combine detection with secure coding practices, routine patching, and strong prevention policies to ensure your systems remain resilient.
Whether you’re pentesting thick clients, managing enterprise IT, or developing secure applications, defending against DLL sideloading starts with understanding how it works and how to break the chain of trust it abuses.
📚 Further Reading
For more in-depth information on DLL sideloading, secure DLL handling, and related Windows API behaviors, explore the following resources:
- 🔒 Secure Loading of Libraries to Prevent DLL Preloading Attacks – Microsoft Support
Microsoft’s official guide on mitigating DLL preloading vulnerabilities through secure coding practices. - 📘 LoadLibraryA Function – Win32 API Reference
Understand how dynamic-link libraries (DLLs) are loaded, and what risks come with improper path handling. - 📘 SearchPathA Function – Win32 API Reference
Documentation on how Windows locates files usingSearchPath—including potential pitfalls. - 📁 ShellExecuteA Function – Win32 API Reference
Learn howShellExecutecan launch executables and how to use it securely to avoid DLL hijacks. - ⚙️ CreateProcessA Function – Win32 API Reference
A deeper look atCreateProcessand how specifying full paths can prevent DLL preloading issues.
