🔍 Introduction
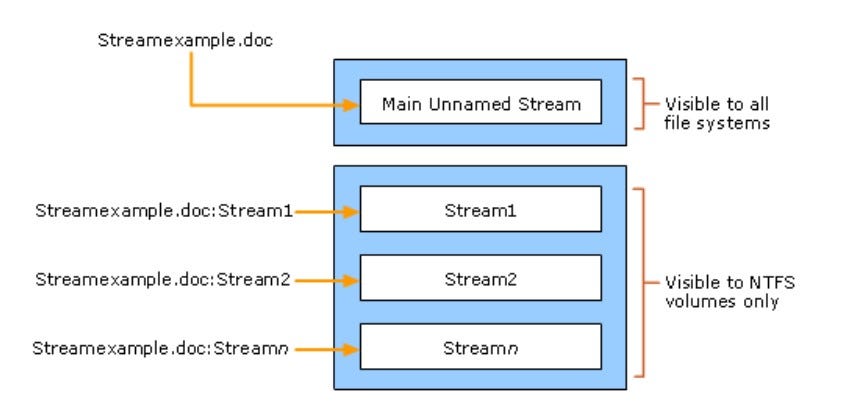
Alternate Data Streams (ADS) are hidden components attached to regular files—such as documents, executables, and system files—on NTFS drives. In this guide, you’ll learn:
- ✅ What ADS are
- ✅ How both legitimate applications and malware use them
- ✅ How to detect and remove malicious ADS safely
To enhance your malware detection skills, consider reviewing Learning HijackThis!.
🧠 A Brief History of ADS
Since their introduction in Windows NT with the NTFS file system, ADS have served a purpose. They were originally designed to maintain compatibility with Apple’s Hierarchical File System (HFS).
📌 Legitimate Uses:
- Applications store metadata such as indexing details and access permissions in ADS.
- Document properties, visible under the “Details” tab, are stored in ADS.
- Antivirus programs might use ADS to log scanning details.
While these uses are valid, attackers frequently exploit ADS for concealment.
🧰 How Software Uses ADS
Legitimate programs commonly utilize ADS to store metadata invisibly. For example, if you create a text file and view its properties, you’ll see summary information stored through an ADS.
➕ Example: Creating ADS via Command Prompt
c:\file.exe > C:\WINDOWS\system32\calc.exe:file.exeCode language: CSS (css)Here, file.exe becomes a hidden stream inside calc.exe. However, the host file’s appearance and behavior remain unchanged.
⚠️ Why ADS Can Be Dangerous
Despite their usefulness, ADS present a security risk when misused.
🚩 Exploitation by Malware:
- ADS are invisible in standard Explorer views and directory listings.
- Malicious streams can be launched via PowerShell, VBScript, or command line.
- Traditional antivirus and Task Manager may fail to detect them.
🚨 Common Risks:
- Trojans, ransomware, or spyware can hide in ADS.
- Rootkits often use ADS to maintain stealth.
- These streams do not alter file size or timestamp, making them hard to detect manually.
❌ Can ADS Be Disabled?
Unfortunately, ADS cannot be disabled in NTFS. Nevertheless, you can scan and remove them using specialized utilities.
🔎 How to Detect and Remove ADS Infections
Manual removal can be risky and may break applications. Instead, it’s better to rely on trusted tools. Keep in mind: deleting a host file will also delete its ADS.
🧰 Trusted Tools for Detection and Removal:
Each of these tools is designed to uncover and eliminate malicious ADS.
🧽 Removing ADS with FRST
🧾 Example from an FRST Log:
AlternateDataStreams: C:\Windows\System32\legitfile:malware.exe [134]
AlternateDataStreams: C:\malware:malware.exe [134]Code language: CSS (css)🛠 Removal Process:
- Download and run FRST.
- In the same directory, create a file named
fixlist.txtwith this content:
Start::
AlternateDataStreams: C:\Windows\System32\legitfile:malware.exe [134]
AlternateDataStreams: C:\malware:malware.exe [134]
C:\malware
Stop::Code language: CSS (css)- Click Fix in the FRST interface.
- Reboot your system once cleanup is complete.
🧽 Removing ADS with OTL (OldTimer’s List It)
🧾 Example from an OTL Log:
@Alternate Data Stream - 48 bytes -> C:\WINDOWS:5E0D2877D3BDDE45Code language: CSS (css)🛠 Removal Steps:
- Launch
OTL.exe. - Under Custom Scans/Fixes, paste the following:
:Files
@C:\WINDOWS:5E0D2877D3BDDE45
:Commands
[purity]
[emptytemp]
[start explorer]
[Reboot]- Click Run Fix.
- Allow your system to reboot.
🧽 Removing ADS with ComboFix
ComboFix detects and removes ADS automatically during its standard scan. However, you can also specify entries manually.
🧾 Example Log Entry:
c:\windows\system32\OLD4.tmp:ext.exe 32768 bytes executableCode language: CSS (css)🛠 Manual Removal:
- Open Notepad.
- Enter the following:
ADS::
c:\windows\system32\OLD4.tmpCode language: CSS (css)- Save it as
CFScript.txt. - Drag this script onto
ComboFix.exe. - Let ComboFix complete the removal process.
🧽 Removing ADS with HijackThis (ADS Spy)
HijackThis includes a utility called ADS Spy, designed to detect and delete hidden ADS entries. It is an effective method of removing ADS infections.
🛠 Removal Instructions:
- Open HijackThis.
- Click Config → Misc Tools → ADS Spy.
- Press Scan to find hidden streams.
- Review the results carefully.
- Select unwanted entries and click Remove Selected.
💡 Need a refresher on HijackThis? See Learning HijackThis!.
✅ Conclusion
Alternate Data Streams (ADS) are integral to NTFS but present risks when exploited. Although you can’t disable ADS, using trusted tools allows you to remove threats effectively.
✅ Employ tools like FRST, OTL, ComboFix, and HijackThis to detect and clean up ADS infections.
🔁 Regular system scans can reveal hidden threats your antivirus might overlook.
🌐 For expanded malware analysis techniques, visit Learning HijackThis! and explore our Malware & Virus Analysis Resources hub.