Introduction to SmokeLoader Malware
SmokeLoader is a long-standing malware downloader that has remained active in the threat landscape since 2011. Known for its modular architecture and consistent evolution, SmokeLoader serves as a launchpad for delivering other malicious payloads. This in-depth timeline examines the malware’s development across its decade-long activity.
In its early years, SmokeLoader employed basic functionality and straightforward distribution. Over time, however, it adopted more advanced features—including custom encryption, obfuscation, plugin support, and anti-analysis methods. These continuous changes allowed it to evade detection and maintain persistence in targeted systems.
Throughout this article, we’ll explore the key innovations and functionality introduced in each major version of SmokeLoader from 2011 through 2022. We will also review command structures, network protocols, plugins, and persistence mechanisms that have been observed in the wild.
🧠 Looking for more analysis on malware families? Check out our deep dive into CoffeeLoader malware for comparative research.
2011–2014: The Evolution Begins
SmokeLoader first appeared around 2011 as a lightweight malware downloader. The early variants were basic but effective: they provided remote operators with the ability to download and execute other malicious files onto infected systems. These initial versions laid the foundation for the modular and highly configurable framework that SmokeLoader would later become.
Initial Design and Basic Loader Functionality
In these formative years, the core loader performed only a few simple actions:
- Contacted hardcoded command-and-control (C2) servers
- Downloaded and executed additional payloads
- Maintained minimal system footprint
- Avoided detection by using custom packers
Version 2014: First Use of Obfuscation and Modular Structure
By 2014, SmokeLoader underwent a significant evolution with the introduction of modular capabilities. This allowed attackers to tailor infections for specific campaigns, loading only the modules necessary for the job. The following changes were notable:
- Bot ID generation: Early versions created bot IDs using the victim’s computer name and disk volume data.
- Encryption: SmokeLoader began employing XOR-based string obfuscation and primitive encryption routines.
- Plugin support: The malware could now load modules such as password stealers or form grabbers dynamically.
- Infection vector: Typically delivered through exploit kits or phishing attachments disguised as invoice PDFs or ZIP archives.
SmokeLoader’s increasing modularity by 2014 made it attractive for a variety of threat actors. In this version, while it had not yet implemented strong encryption or robust anti-analysis features, it laid the groundwork for those enhancements in subsequent years.
💡 Tip: Interested in understanding modular malware structures? Explore our post on thick vs. thin clients and DLL sideloading for insight into attack delivery strategies.
2015–2017: Protocol Renaissance
Between 2015 and 2017, SmokeLoader introduced a complete redesign of its communication protocols and began enhancing its evasion techniques. These improvements established the core architecture that would be reused and slightly evolved over the next several years.
Network Protocol Overhaul
In version 2015, SmokeLoader revised its command-and-control (C2) protocol. The malware began sending data fields separated by the # delimiter in plaintext. These fields, shown in the table below, became standard across all future versions.
Table 1: SmokeLoader C2 fields in versions 2015–2022.
Transition to Binary Protocol with RC4 Encryption
Starting in 2017, SmokeLoader transitioned to a binary protocol while maintaining the same fields. Each packet was encrypted using static 4-byte RC4 keys—one for encrypting the request and another for decrypting the response. These keys were hardcoded into the main module, which made network detection and decryption significantly harder unless the keys were known.
A new field was added in version 2020 to include the victim’s computer name. Below is an example network packet (with RC4 encryption removed):
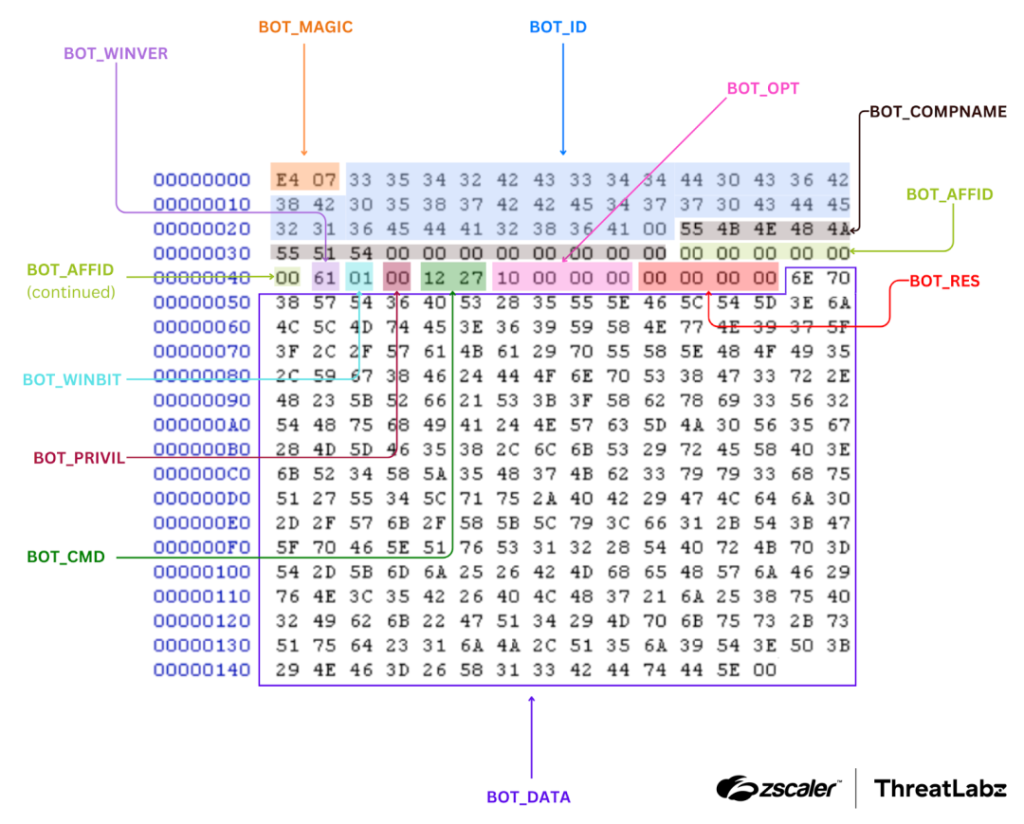
Figure 1: Example SmokeLoader 2020–2022 network data (RC4 encryption removed).
Implemented Command IDs
SmokeLoader added multiple command IDs for modular operations. Below is a summary of implemented commands from 2017–2022:
Table 2: Command IDs used by SmokeLoader versions 2017–2022.
Server Responses
The primary command CMD_ONLINE acts as a keep-alive. The server responds with one of these options:
Table 3: C2 server responses.
If the server provides tasks, they may include plugin configuration data:
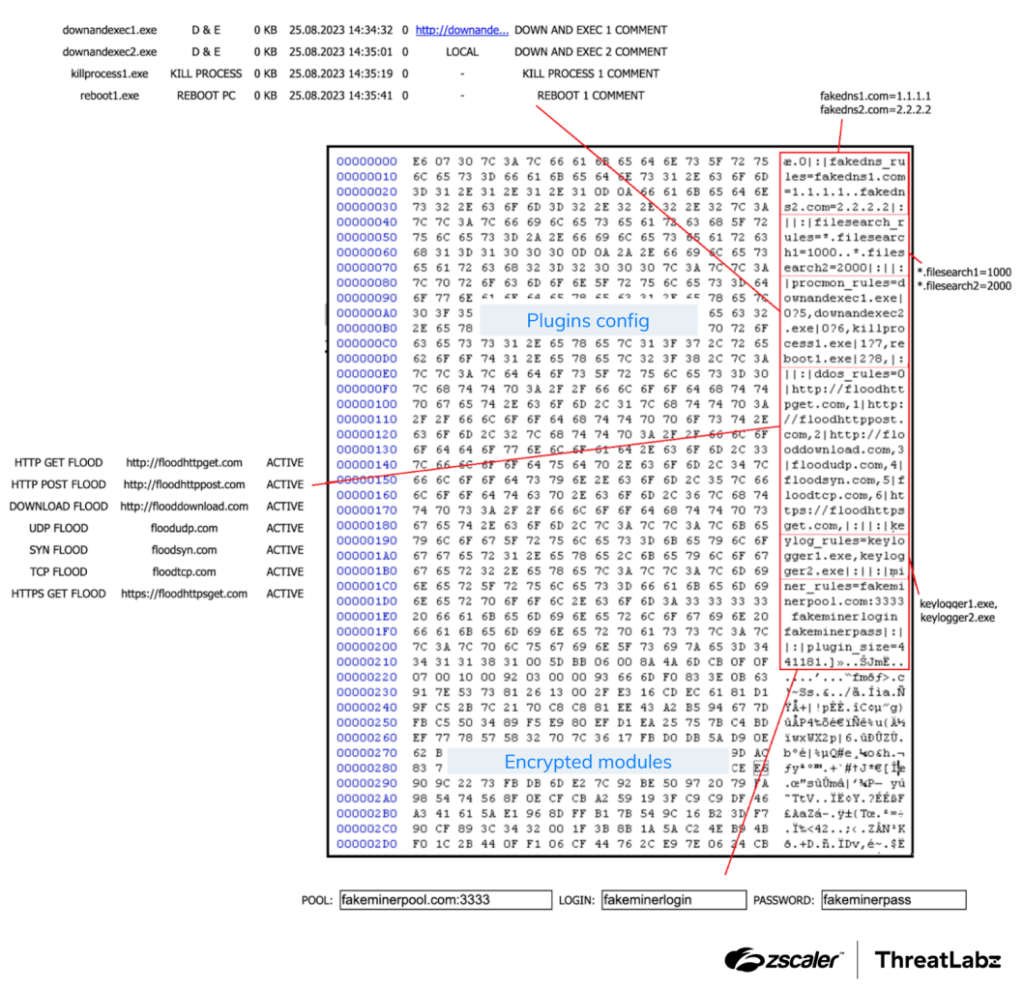
Figure 2: Example SmokeLoader task with plugins and configuration.
Operation Endgame (May 2024)
In Operation Endgame, Zscaler ThreatLabz and partners issued uninstall commands across infected machines, exploiting the malware’s built-in 0x72 “uninstall” command to disinfect tens of thousands of systems.
Algorithm Modifications
In this era, SmokeLoader replaced many static methods with version-specific algorithms:
- Bot ID generation: Migrated from CRC32/XOR to MD5.
- C2 encryption: Version 2017 introduced a custom XOR-based C2 obfuscation algorithm.
def smoke2017_c2_xor_decrypt(enc, key):
out = b''
i = 0
while True:
out += (((enc[i] ^ key[0]) -
(enc[i+1] ^ key[0])) & 0xff).to_bytes(1, 'little')
i += 2
if i > len(enc) / 2:
break
return out
Code language: PHP (php)- API hashing: Also in 2017, the malware replaced its API resolution algorithm with a hash-based lookup.
def calc_hash_smoke2017(name):
name = name.encode()
hash = 0
for i in range(0, len(name)):
hash ^= (name[i] << 8)
temp = ROL(hash, 8)
temp_bytes = list(struct.pack('<L', temp))
temp_bytes[0] = 0xff & (temp_bytes[1] ^ temp)
temp = struct.unpack('<L', bytes(temp_bytes))[0]
hash = 0xffffffff & (temp * 2)
return hashCode language: PHP (php)2018: The Stager Revolution
The release of SmokeLoader version 2018 marked a major architectural shift. Most notably, the malware introduced a significantly enhanced stager module, which not only loaded the main payload but also incorporated extensive anti-analysis and obfuscation features.
Enhanced Stager with Process Injection
The stager underwent a major transformation in how it handled execution:
- In version 2017, the stager created a new
explorer.exeprocess and injected the main module into it, since the payload was 32-bit and needed to run even on 64-bit systems. - From version 2018 onward, the stager injected the main module directly into the existing
explorer.exeprocess. It also bundled both x86 and x64 versions of the payload to support all architectures.
Code Obfuscation Techniques
To complicate static analysis, several obfuscation methods were introduced starting in 2018. These techniques were designed to confuse disassemblers and reverse engineering tools:
- Code permutations
- Opaque predicates using conditional jumps like
JZ/JNZ - Stack-based code mixed with string data
- Obfuscated jumps using RVA and precalculated image base
These techniques made the stager far more resistant to traditional disassembly.
Encrypted Functions and Decryption Logic
Earlier versions of SmokeLoader used simple XOR obfuscation. However, from version 2018, the stager encrypted a majority of its code using nested XOR encryption layers.
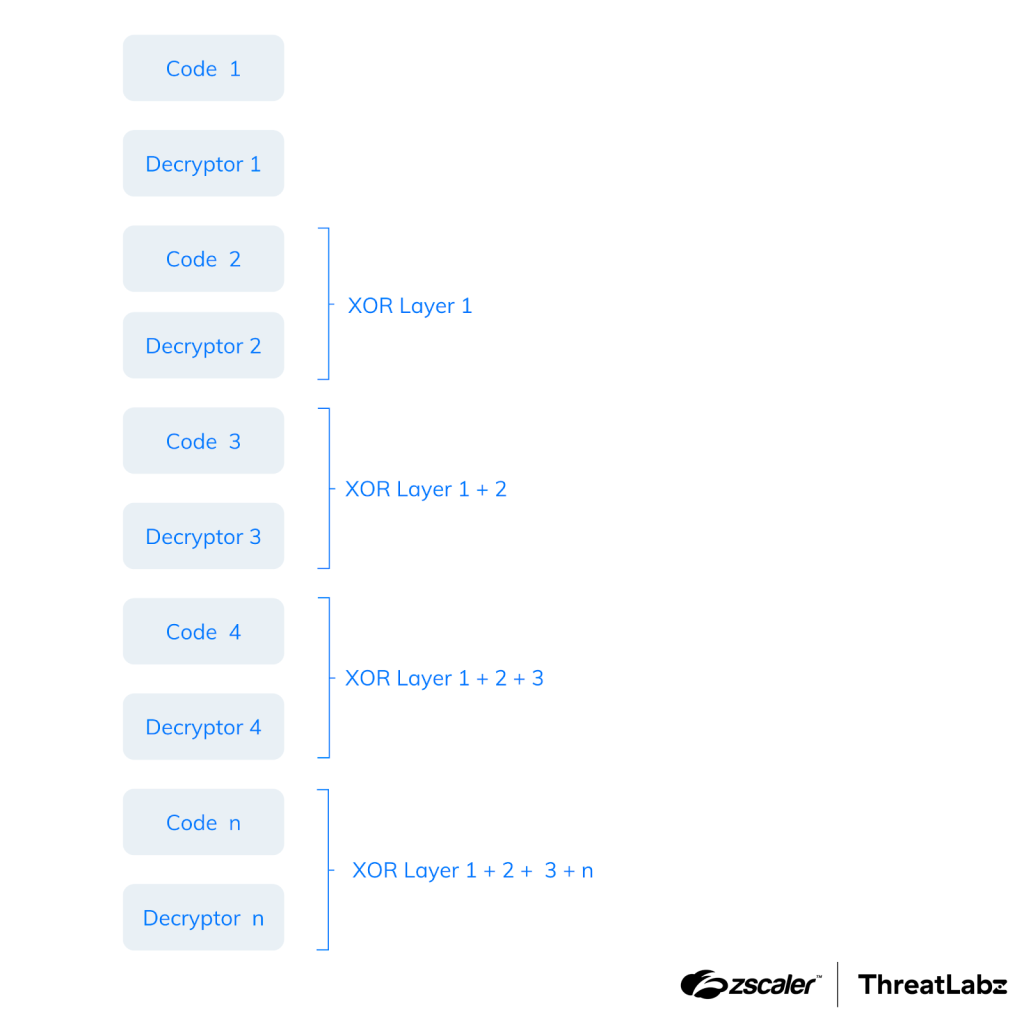
Figure 3: SmokeLoader’s stager using nested XOR encryption layers.
The decrypted code blocks were immediately re-encrypted after execution to minimize memory exposure. A dedicated decryption function was used for this purpose:
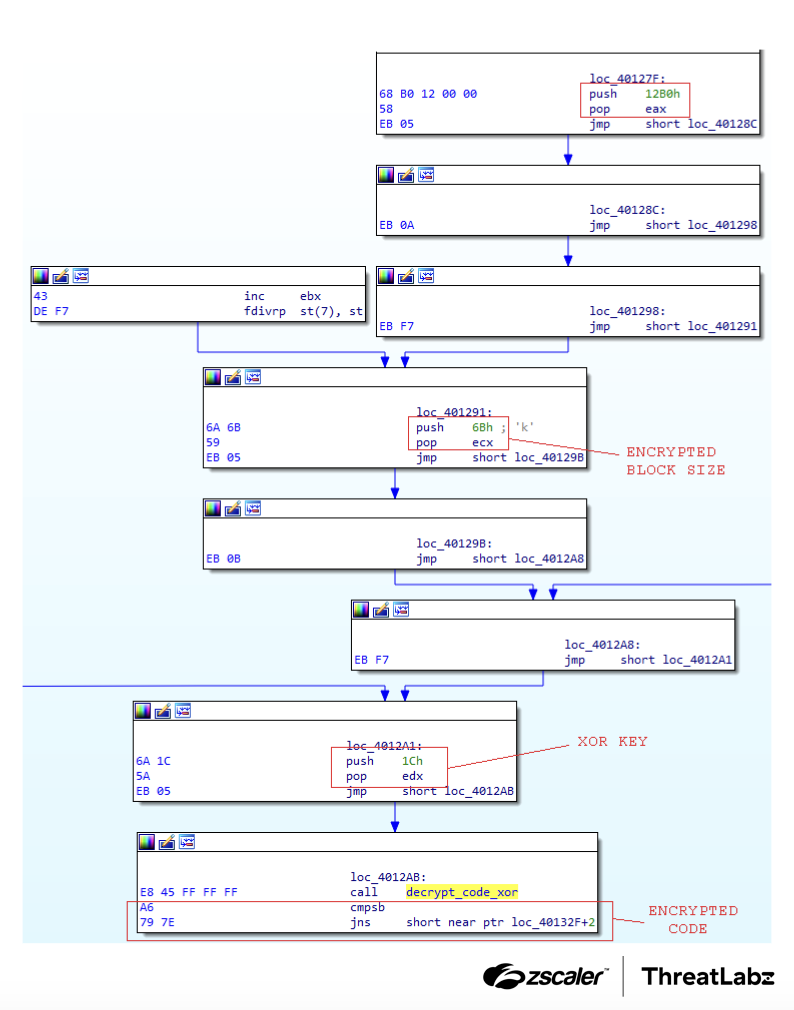
Figure 4: Code decryption for SmokeLoader versions 2018–2022
Expanded Anti-Analysis Capabilities
The stager took over many anti-analysis tasks that had previously resided in the main module. Over time, new versions added further evasion techniques:
- API resolution via DJB2 hashing algorithm
- Language-based geofencing: Checks for Ukrainian or Russian keyboard layouts
- OS version checks: Refuses to run on Windows versions earlier than Vista (OS major version < 6)
PROPagate Injection Technique
In version 2018, SmokeLoader introduced PROPagate injection, using Windows APIs like:
NtOpenProcessNtDuplicateObjectNtCreateSectionNtMapViewOfSectionSetPropASetNotifyMessageA
These allowed stealthy injection into explorer.exe without using common, detectable API calls.
Algorithm Changes (C2 Decryption & API Hashing)
A variety of new algorithms were adopted to further thwart detection:
- C2 URL encryption used a 4-byte XOR key.
- Decompression of the main module was done using the Windows API
RtlDecompressBufferwith the LZNT1 algorithm. - Scheduled tasks were introduced for persistence, replacing other methods.
Python – C2 URL Decryption (2018)
def smoke2018_c2_xor_decrypt(enc, key):
out = ''
for i in range(len(enc) - 4):
xor_key = struct.unpack('<L', key)[0]
v = struct.unpack('<L', enc[i:i + 4])[0]
for j in range(4):
v = v ^ xor_key
xor_key >>= 8
tmp = chr(~v & 0xff)
out += tmp
return out.encode()
Code language: JavaScript (javascript)Python – API Hashing Algorithm (2018–2022)
def calc_hash_smoke2018_2022(name):
name = name.encode()
hash = 0
for i in range(len(name)):
hash = 0xffffffff & ((name[i] & 0xDF) +
ROL(hash ^ (name[i] & 0xDF), 8))
return hash
Code language: JavaScript (javascript)Each subsequent version preserved these techniques while slightly adapting encryption keys, compression strategies, or process injection behavior.
2019–2022: Contemporary History of SmokeLoader Malware
While the core structure and behavior of SmokeLoader remained mostly consistent in recent years, new versions introduced sophisticated changes in anti-analysis, decryption, and environmental awareness.
NTDLL Hook Evasion
One of the standout upgrades in versions 2019 through 2022 was the evasion of API monitoring tools that rely on function hooks within ntdll.dll.
To avoid these hooks:
- Version 2019: Created a physical copy of
ntdll.dllin the%TEMP%directory, then loaded it usingLdrLoadDll. - Versions 2020–2022: Created an in-memory mapped copy using
CreateFileMappingWandMapViewOfFile, avoiding disk-based artifacts.
This ensured that if breakpoints or userland hooks were placed on standard API calls, they would be rendered ineffective.
Security Product Detection
Each version expanded its arsenal of techniques to detect virtualized or monitored environments. These included string checks, service enumeration, and registry lookups. The table below documents this evolution.
These changes reflect a growing focus on evading sandbox analysis, hypervisor detection, and virtual drivers.
Additionally, newer variants used NtQuerySystemInformation and NtQueryInformationProcess to inspect kernel flags like SystemCodeIntegrityInformation and ProcessDebugPort.
Algorithm Updates in Recent Variants
SmokeLoader has always relied on encryption and compression to conceal configuration data and payloads. Versions 2019–2022 introduced the following changes:
- 2019 & 2020: Used a custom XOR-based decryption algorithm for C2 lists. The XOR key was derived from the CRC32b of the encrypted data.
Python – Decryption Routine (2019–2020)
def smoke2019_2020_decrypt(enc, key):
dec = b''
for c in enc:
for i in key:
c = c ^ i
dec += (c ^ 0xE4).to_bytes(1, 'little')
return dec
Code language: JavaScript (javascript)- 2022: Adopted RC4 encryption to protect C2 configurations. The RC4 key and the CRC32b value were stored inside a structure:
C – C2 Structure (2022)
struct EncryptedC2 {
unsigned char C2_length;
unsigned int RC4_key;
unsigned char C2_encrypted_data[C2_LENGTH];
unsigned int C2_CRC32b;
};
Compression Algorithm Updates
SmokeLoader also moved away from Windows-native LZNT1 compression:
- 2018: Used
RtlDecompressBufferwith LZNT1 - 2020 & 2022: Switched to LZSA, a newer compression algorithm
Injection Strategy Modifications
The previously used PROPagate injection technique was deprecated. Versions 2020 and 2022 transitioned to:
- Creating a shared section between the stager and explorer process
- Spawning a remote thread using
RtlCreateUserThread
This new method was more streamlined and stealthier than the older SetPropA and SetNotifyMessageA approach.
Conclusion
SmokeLoader malware continues to stand out due to its sustained development, modular architecture, and deep anti-analysis capabilities. Over the years, its developers have constantly evolved its payload delivery mechanisms, encryption algorithms, and sandbox evasion techniques to maintain stealth and effectiveness.
The most recent variant observed dates to 2022, and although Operation Endgame significantly disrupted its distribution, there are indications that activity may resume. Threat actors historically using SmokeLoader are likely to retool and adapt, potentially integrating the malware into new delivery ecosystems.
For defenders, this means vigilance must remain high — particularly regarding loaders that deliver secondary payloads like infostealers, ransomware, and espionage tools.
Zscaler Coverage
Zscaler’s multilayered cloud-native platform provides detection across network, endpoint, and sandbox layers.
Threats are detected under labels such as:
Indicators of Compromise (IOCs)
Below is a summary of SHA256 file hashes for known SmokeLoader samples by year:
| Year | SHA256 |
|---|---|
| 2012 | 857fc7aafbbf0d4c850c1b1585a72420600bdabe269f343c0c817614aa6c94cd |
| 2014 | e92d1c2c1e145c1d6c42dd402e75f46e5edfb2bab5539c4d103d345b5ac965a3 |
| 2016 | 18aa1b79bbeee6a731b897377233d54b1b2464eeb9a25dafc0debfc43af8c04f |
| 2017 | 32ba1f3b96cf77a08c041d4983d6afa7db8e1948d27d6a8dd55b7bb95e493189 |
| 2018 | b6ec96043dba7722cac4ed24b6979fc71a758bdf18ca44353c19194c172bf621 |
| 2018 | 5727c2cd54b8408ca0f8e943cad61027a2c3d51da64f2f1224a6b9acc4820f8e |
| 2019 | fc20b03299b8ae91e72e104ee4f18e40125b2b061f1509d1c5b3f9fac3104934 |
| 2019 | d5efd66f54dce6b51870e40a458fa30de366a2982ab2f83dddff5cb3349f654d |
| 2020 | 070a94ee0cd9ac1b1ed467353f5731e09cab136315447c04f53bc52d4fe3f8cc |
| 2020 | 7377efde4e4e86650ab8495f57ab4a76d4f8efe31e2962305b8c42a6cee70454 |
| 2022 | c78bc4fb8955940b3ac9b52cb16744a61f8bdaf673fd64fc106465241c56cc6c |

