A website launched by Elon Musk’s Department of Government Efficiency (DOGE) recently became the center of controversy after it was discovered to contain a severe security flaw. In this high-profile case of the DOGE website hacked, unauthorized users were able to modify live content directly on the government platform.
What Went Wrong?
The issue stemmed from the website’s use of an unsecured external database. According to two experienced web development experts, this exposed the DOGE website to public modification. Anyone with knowledge of the vulnerability could upload and display content on the official page.
Initially launched in January, the site remained mostly static for weeks—featuring only a few lines of text and a cartoonish logo. However, as soon as the vulnerability was made public, it became a target for satirical and unauthorized posts.
How Was the DOGE Website Hacked?
First reported by 404Media, the security oversight was discovered when developers noticed the site was connecting to a modifiable backend. Specifically, it was tied to a Cloudflare Pages setup that lacked adequate authentication controls. Consequently, third parties could change the site content with ease.
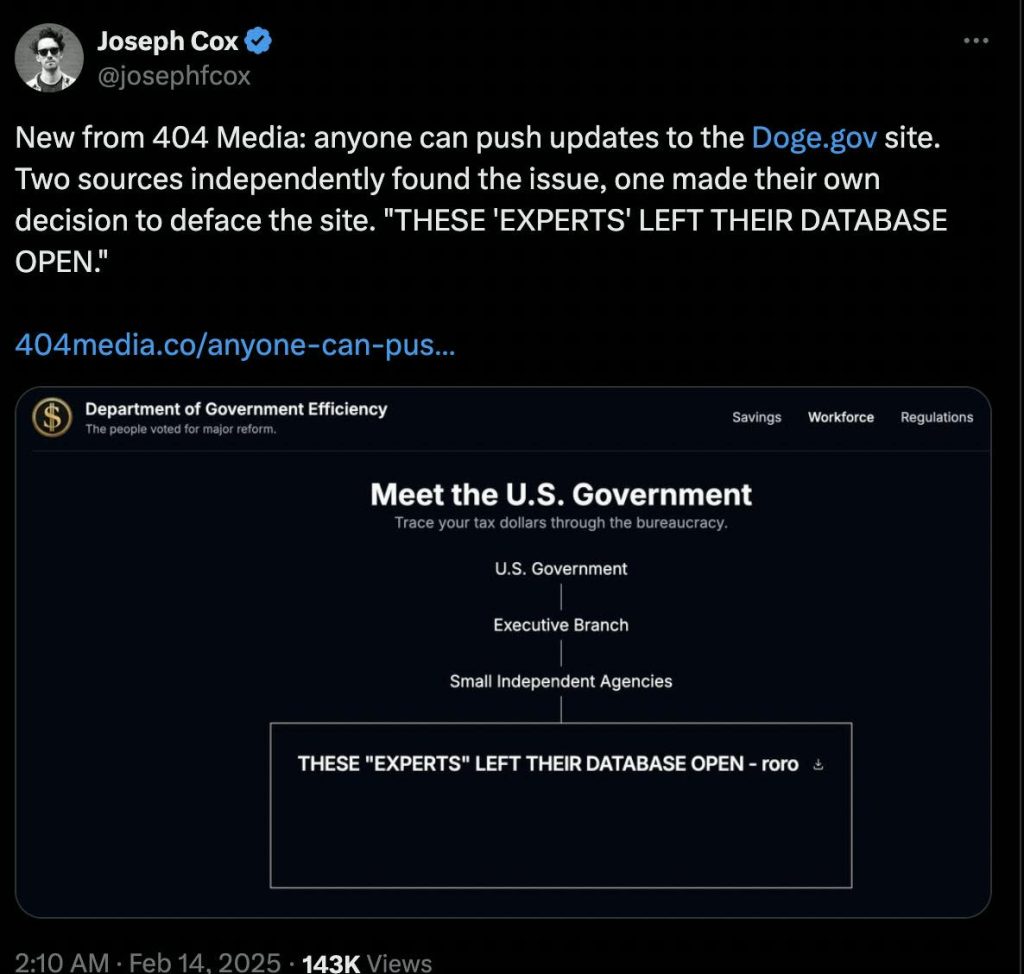
Not long after, users began exploiting the flaw. Satirical messages appeared on the homepage, including:
- “This is a joke of a .gov site”
- “THESE ‘EXPERTS’ LEFT THEIR DATABASE OPEN – roro”
These posts remained online for several hours, drawing further scrutiny. Even Newsweek confirmed the messages were visible the following morning.
Underlying Concerns
Many experts believe the breach happened due to rushed development and poor security hygiene. One coder told 404Media: “It feels like it was hastily constructed.” Additionally, they observed errors and exposed sensitive information within the page’s source code.
Sam Curry, a coding expert, noted the website was developed and hosted by Burst Data, a company reportedly linked to a current DOGE employee. Moreover, the site used Cloudflare’s ImageDelivery service to route assets—further hinting at a rushed setup.
Although the DOGE team has since fixed the issue and removed the messages, the DOGE website hacked incident raises broader concerns about how the department manages security and classified data.
Did DOGE Expose Classified Intelligence?
Alarmingly, reports suggest the DOGE website may have displayed classified intelligence information prior to the breach. The Huffington Post stated that details about the size and staffing of a U.S. intelligence agency were visible on the site.
This incident not only exposed weak cybersecurity practices but also posed potential risks to national security. Critics are now questioning DOGE’s access to sensitive information and whether proper safeguards are in place.
Legal Fallout and Public Reaction
In the aftermath of the DOGE website hacked event, several lawsuits have reportedly been filed. These legal challenges aim to scrutinize DOGE’s data access policies and address any potential conflicts of interest within the department.
Public trust has been shaken, and cybersecurity professionals are urging stronger safeguards for government-backed websites moving forward.
Conclusion
The DOGE website hacked incident stands as a stark reminder that even official government domains can fall prey to basic security lapses. In today’s digital world, where public data, trust, and national security are on the line, every organization—especially those operating under a .gov domain—must implement robust security practices from the start.
📚 Further Reading
For more real-world examples of security vulnerabilities and how they’re discovered, reported, and mitigated, check out these related guides:
- 🔐 Google Chrome Exploit CVE-2025-2476
Learn how a use-after-free vulnerability in Chrome’s Lens component was discovered and how to stay protected from browser-based exploits. - ☁️ How to Fix Apache Tomcat Exploit CVE-2025-24813
Dive into the Apache Tomcat exploit affecting the CGI Servlet and explore step-by-step remediation strategies for securing web application infrastructure.
These resources offer critical insight into software flaws and are essential for developers, sysadmins, and security researchers alike.